Inherent Security Policies Between ASA Interfaces
In addition, there are two cases in which it is not possible to assign unique security levels
to each ASA interface:
■ The number of ASA interfaces is greater than the number of unique security
level values: Because the security level can range from 0 to 100, there are 101
unique values. Some ASA platforms can support more than 101 VLAN interfaces, so
it becomes impossible to give them all unique security levels. In this case, you can
use the following command in global configuration mode so that you can reuse security
level numbers and relax the security level constraint between interfaces.
ciscoasa(config)# same-security-traffic permit inter-interface
■ Traffic must enter and exit through the same interface, traversing the same
security level: When an ASA is configured to support logical VPN connections,
multiple connections might terminate on the same ASA interface. This VPN architecture
looks much like the spokes of a wheel, where the ASA interface is at the hub or
center. When traffic comes from one VPN spoke and enters another spoke, it essentially
enters the ASA interface and comes out of one VPN connection, only to enter a
different VPN connection and go back out the same interface. In effect, the VPN
traffic follows a hairpin turn on a single interface.
If an ASA is configured for VPN connections, you can use the following command in
global configuration mode to relax the security level constraint within an interface
ciscoasa(config)# same-security-traffic permit intra-interface
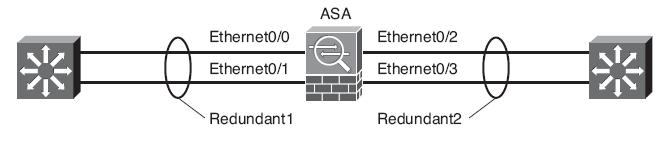
Configuring Interface Redundancy
By default, each physical ASA interface operates independently of any other interface.
The interface can be in one of two operating states: up or down. When an interface is
down for some reason, the ASA cannot send or receive any data through it. For example,
the switch port where an ASA interface connects might fail, causing the ASA interface to
go down too.
To keep an ASA interface up and active all the time, you can configure physical interfaces
as redundant pairs. As a redundant pair, two interfaces are set aside for the same ASA
function (inside, outside, and so on), and connect to the same network. Only one of the
interfaces is active at any given time; the other interface stays in a standby state. As soon
as the active interface loses its link status and goes down, the standby interface becomes
active and takes over passing traffic.
Both physical interfaces in a redundant pair are configured as members of a single logical
“redundant” interface. In order to join two interfaces as a redundant pair, the interfaces
must be of the same type (10/100/1000BASE-TX, for example).
The redundant interface, rather than its physical member interfaces, is configured with a
unique interface name, security level, and IP address—all the parameters used in ASA
interface operations.
First, you must create the redundant interface by entering the following configuration
command:
ciscoasa(config)# interface redundant number
You can define up to eight redundant interfaces on an ASA. Therefore, the interface
number can be 1 through 8.
Next, use the following command to add a physical interface as a member of the redundant
interface:
ciscoasa(config-int)# member-interface physical_interface
Here, physical_interface is the hardware name and number, like ethernet0/1 or gigabitethernet0/
1, for example.
Configuring a Redundant Interface Pair
ciscoasa(config)# interface redundant 1
ciscoasa(config-if)# member-interface ethernet0/0
INFO: security-level and IP address are cleared on Ethernet0/0.
ciscoasa(config-if)# member-interface ethernet0/1
INFO: security-level and IP address are cleared on Ethernet0/1.
ciscoasa(config-if)# no shutdown
http://haneeftechtips.blogspot.com/




No comments:
Post a Comment